News Story
Securing IC encryption during manufacturing and testing
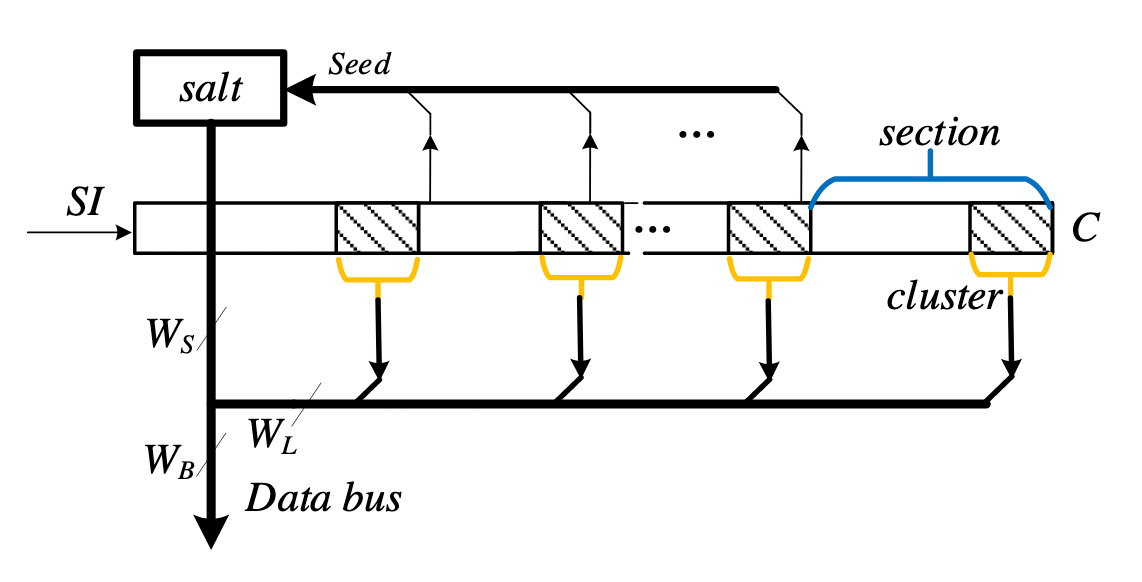
Section in a scan chain and a cluster in a section. (Fig. 5 from the paper)
As both the complexity of integrated circuit (IC) designs and the impact of fabrication variation have dramatically increased, testing during the manufacturing process has become an indispensable part of guaranteeing IC yield. To improve testing efficiency, many design-for-testability (DfT) techniques have been widely adopted. Typically, specific design structures are built into the ICs that allow them to cooperate with external automatic testing equipment.
“Scan design” is a DfT technique that provides high controllability and testability. However, attackers can use scan design as a side channel to access intermediate encryption results and easily deduce a cipher key. This is a problem for cryptographic chips in particular, as the sensitive information inside the chip can leak through the scan chain. Many successful attacking scenarios hack cryptographic chips by analyzing the intermediate encryption results obtained from the scan chain, revealing the cipher keys.
To resist such attacks, many countermeasures have been proposed that obfuscate the test data in the scan chain. Unfortunately, because of performance and resource constraints, there is still a high risk of the correct test data being obtained, even from the obfuscated output.
A new paper published in the March 10, 2020 issue of IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems proposes securing the scan design by using the cryptographic hash module for post processing test responses. “A Guaranteed Secure Scan Design based on Test Data Obfuscation by Cryptographic Hash” was written by Aikiao Cui and Mengyang Li of the School of Electronic and Information Engineering, Harbin Institute of Technology, Shenzhen, China; Professor Gang Qu (ECE/ISR); and Huawei Li of the Institute of Computing Technology, Chinese Academy of Sciences, Beijing, China.
The test response is processed by a cryptographic hash function prior to being unloaded, and the property of pre-image resistance of hash guarantees that one cannot recover the original test response from the hash value. Because of this, an adversary has no way to obtain the intermediate encryption result or deduce the cipher key unless he can crack the hash function.
The authors’ new approach has several clear advantages over existing ones. First, the security is guaranteed based on the pre-image resistance of cryptographic hash function and introduced salt information and data collection scheme. Second, it incurs low overhead because the hash module is normally available on the IC, especially ICs where security is important. Finally, full testability is retained as the approach does not modify test input. The design does not affect the testing process and the testability of original design is maintained.
The authors demonstrate that their approach can resist all known scan-based side-channel attacks. Compared with many countermeasures based on obfuscation of scan data, it is more secure; the transformation of test response is one-way only and can resist potential attacks based on the analysis of obfuscation logic and design detail.
Published April 21, 2020